| Published: Date: Updated: Author: |
The Bahamas Investor Magazine January 21, 2015 January 21, 2015 Diveane Bowe (right) and Micho Schumann (left) |
As financial services providers in The Bahamas increasingly enhance their product offerings through the use of technology, cyber security is becoming an important issue for companies and individuals concerned about breaches in computer networks and the theft of private information.
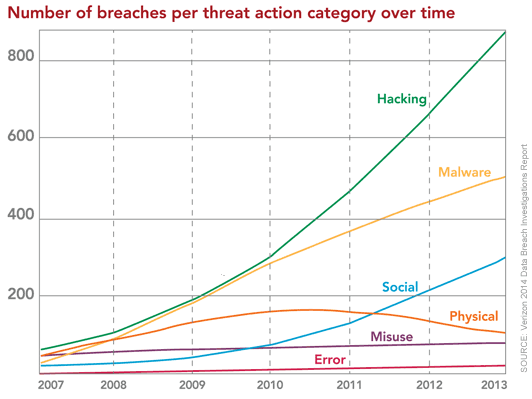
Top graphic: Excerpt from the 2014 Data Breach Investigations Report (Source: Verizon Enterprise Solutions)
According to a recent survey by the US Secret Service and PriceWaterhouseCoopers, the threat of cybercrime around the world is on the rise, with three out of four of 500 major US corporations saying that they detected an increase in security breaches last year. The average number of security intrusions was 135 per organization. A recent example of how security can be breached is Heartbleed, a flaw found in OpenSSL, which is a software product used by millions of websites and network devices to provide secure connections. Software engineers had discovered an error within the OpenSSL code that could allow hackers to access parts of a web server’s memory containing sensitive information, such as client data. It is estimated that at some point a fifth of all websites ran a vulnerable version of OpenSSL.
Even more recently, a number of well-known companies have been successfully attacked. In some of these cases, millions of credit card numbers were compromised.
In order to combat this recent global trend, Inter-American Committee against Terrorism (CICTE) of the Organization of American States (OAS) conducted a two-day workshop in Nassau last year as a part of the technical assistance to be provided to The Bahamas for the development of a National Cyber Security Strategy. The workshop included discussions on a strategy to establish a national Computer Incident Response Team (CIRT). The Technical Mission was led by cyber security specialists from the OAS, with the participation of an expert consultant in the area of CIRT development.
Representatives from 20 key government ministries, corporations and departments attended the workshop.
Executive secretary of CICTE Neil Klopfenstein said at the time that the increasing sophistication of The Bahamas’ banking and commercial sectors, coupled with its relatively high income per capita in the region, made the nation a target for hackers and Internet fraud. “The development and implementation of a National Cyber Security Strategy in our current global context will allow The Bahamas to join other states in the fight against cybercrime.”
The visit formed part of a larger offer of assistance aimed at helping The Bahamas to develop protective mechanisms for cybercrime, and includes follow- up support to facilitate the expedient development and adoption of the strategy.
Minister of National Security Bernard Nottage noted that “the issue of cybercrime, and how the criminal justice system deals with it, is becoming more and more important given the rise in the use of the Internet and the country’s increasing reliance on systems that are vulnerable to new forms of attack.”
In October last year, the Office of the Data Protection Commissioner, along with the Department of Information Technology and the Cyber Crime Unit of the Royal Bahamas Police Force, held a follow- up symposium on data protection.
Regular checks
As well as a national cyber security programme, the recent global hacking incidents highlight the need among Bahamian companies to perform their own regular tests on computer networks to assess their vulnerability to hackers. To identify and remediate security weaknesses, companies should conduct tests that attempt to breach network defenses.
Normally, the organization will test the vulnerability of the corporate website, the e-mail server and other critical systems. But many companies that conduct these tests often fail to fully test web applications that are just as important as the corporate website, firewall and other network components. Financial services companies and law firms, for example, operate a wide range of web applications. These web applications are prime targets for attacks.
Web applications are usually accessed via a web browser, such as Internet Explorer, Google Chrome or Apple Safari. Some web applications used by financial services companies give clients access to their portfolios and their personal information and enable clients to perform a variety of operations ranging from trading stocks to performing money transfers. Even though clients normally require a username and a password, web applications can be a gateway for hackers to gain access to customers’ bank accounts, corporate networks, databases and corporate data.
Companies should also be concerned about the possibility of legitimate clients, as well as hackers, gaining unauthorized access and looking for gaps and weaknesses in the web application’s defenses. The purpose could be financial, credit card or identity fraud. Other possible motivations are corporate espionage or retaliation. The attacker will most likely attempt to gain full access to the company’s database of clients, perform unauthorized transactions or view confidential data. These types of breaches often go undetected by the company; and yet, the implications of such a security breach are enormous. Hackers or rogue clients can steal millions of dollars from customers’ accounts or take personal or corporate information and sell it on the black market. The loss of reputation to the company can be extremely significant. This is why it is essential that organizations perform regular checks to make sure their online presence is secure.
Insider threat
Organizations also need to consider the insider threat. An insider threat can be defined as an employee or consultant who has access to the internal corporate network and its resources and who has malicious intent. These individuals may seek to gain access to corporate secrets, client data or even payroll information. The actions may take place over years and are often difficult to detect. Regular security audits that cover password controls, revoking accounts of terminated employees and periodic review of access permissions are all tasks that will assist in mitigating the insider threat.
Furthermore, in case a breach does happen, multiple layers of security will likely be an organization’s saving grace. The fact that a hacker gained access to systems in itself is obviously not an incident to be pleased about. However, if the organization created a layered approach to security, the fallout may be largely mitigated. For example, a hacker that was able to download an entire database of credit card numbers will be foiled, if the credit card data is properly encrypted. Organizations that store sensitive data need to consider various scenarios that may occur. A firewall and patching are no longer sufficient; multiple layers of security need to be in place.
Test of networks
Organizations should always test the security of external networks as well as web applications. If weaknesses are identified, changes can be made as soon as possible. When a new web application is being developed, testing is critical. The developers should always test for security weaknesses as part of their overall development process. However, once the developers complete their own testing, the web application should be formally tested for vulnerabilities by an independent third party, such as a quality assurance team or an outside organization.
By this stage, it is not appropriate for the programmers to perform the tests, because they should not audit their own work. Furthermore, when the application is later altered or when a new version is produced, security testing should be performed again to ensure no new vulnerabilities are introduced.
Also, web applications and external networks should ideally be retested on an annual basis, since previously unknown weaknesses may be discovered by hackers, exposing the web application to a possible breach. This is especially true for organizations that host and maintain financial and personal data.
With appropriate testing, organizations can be confident they are offering their clients a secure way to perform online operations. The Heartbleed flaw, as well as other high profile hacking incidents recently witnessed, won’t be the last time the alarm is sounded about a possible breach in Internet security. Bahamian companies should prepare for the next one by conducting security checks on a timely basis.
Diveane Bowe (small photo, right) is a partner with KPMG in The Bahamas and leads the IT Advisory Services Practice. Bowe has led security engagements involving a review of IT General Controls, Application Assessments, IT Governance and Penetration Testing.
Micho Schumann (small photo, left) is a senior manager with KPMG’s IT Advisory Group in the Cayman Islands. He holds a master’s degree in information systems, is a Certified Information Systems Security Professional (CISSP) and a Certified Information Systems Auditor (CISA). Schumann has more than 14 years of IT security experience, working extensively with financial institutions, government agencies and high-technology firms.